2026 Browser Data Reveals Major Enterprise Security Blind Spots
Mar. 5th, 2026 10:01 amPolice dismantles online gambling ring exploiting Ukrainian women
Mar. 5th, 2026 07:39 amWindows File Shredder: When deleting a file isn’t enough
Mar. 5th, 2026 11:07 amMost of us think deleting a file means it’s gone for good. But “delete” on a Windows device often just means “out of sight,” not necessarily “out of reach.”
That’s where File Shredder, a new feature within Malwarebytes Tools for Windows, comes in. File Shredder lets you securely delete files from your hard drive or USB drive, so the files are not just removed—but completely unrecoverable, even with specialized recovery software.
What File Shredder does differently
When you delete a file by placing it in your Recycle Bin and emptying the contents, your computer typically removes the reference to it—but the data itself can remain on the drive until it’s overwritten. That leftover data can sometimes be recovered using basic digital tools, some of which can even be downloaded for free online. These data traces pose a problem if the file you want to delete includes personal, financial, or other sensitive information, like tax documents, scanned IDs, contracts, or anything else you would like to remain private forever.
File Shredder goes beyond standard deletion by instead permanently overwriting the file data, ensuring it can’t be reconstructed or recovered. Once a file is shredded, it’s gone for good—no undo, no recovery, no second chances.
That makes File Shredder especially useful when:
- You’re cleaning up sensitive files before selling or donating a device
- You need to securely remove files from a USB drive
- You’re minimizing digital clutter without leaving data behind
- You want peace of mind that private files stay private
How to use File Shredder
File Shredder is designed to be powerful without being complicated.
To use File Shredder:
- Open the Malwarebytes app and select the “Tools” icon from the lefthand menu (the screwdriver and wrench icon)
- From this menu, find and click on “File Shredder”
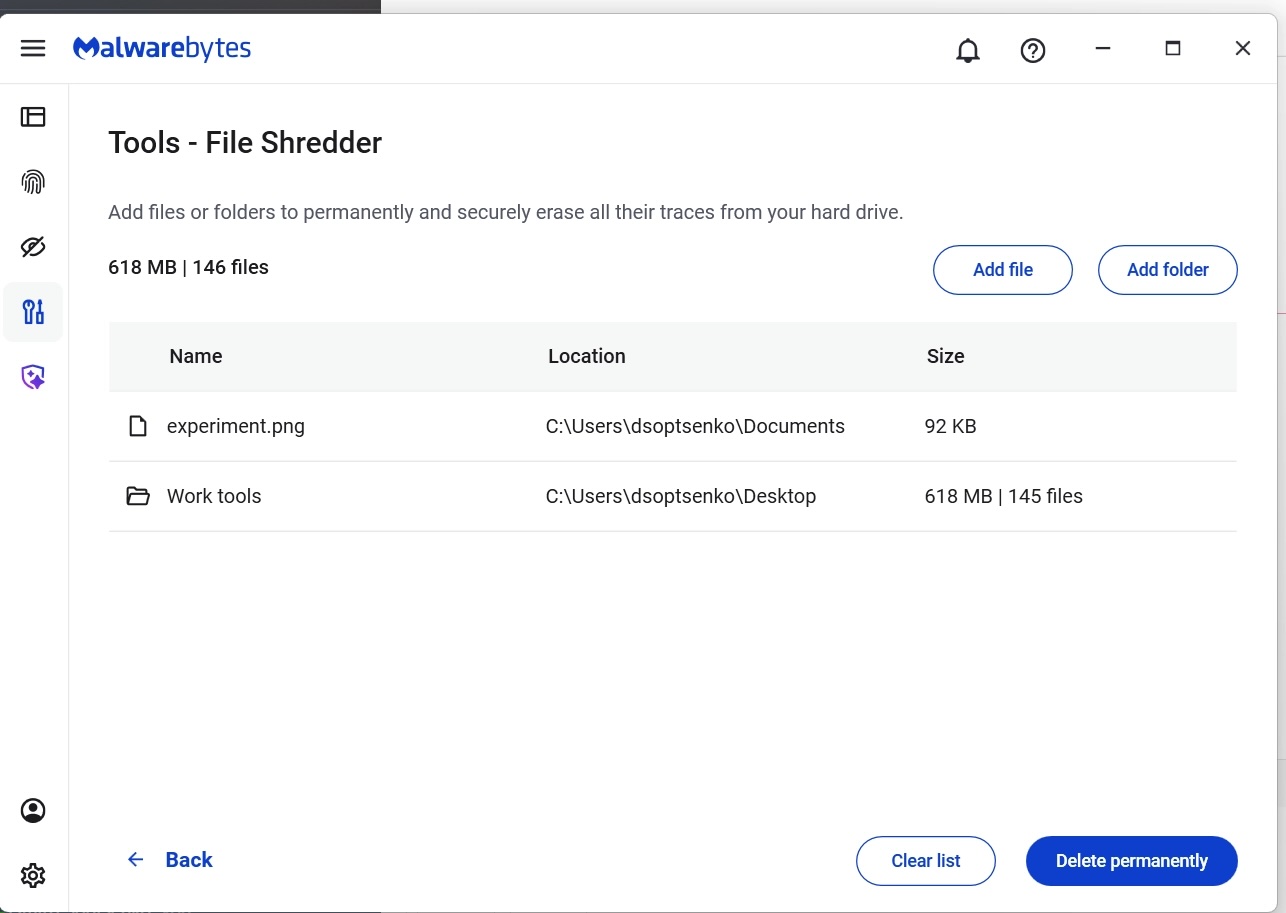
- Once here, you can manually add files or folders to the list and then click on the button “Delete permanently”
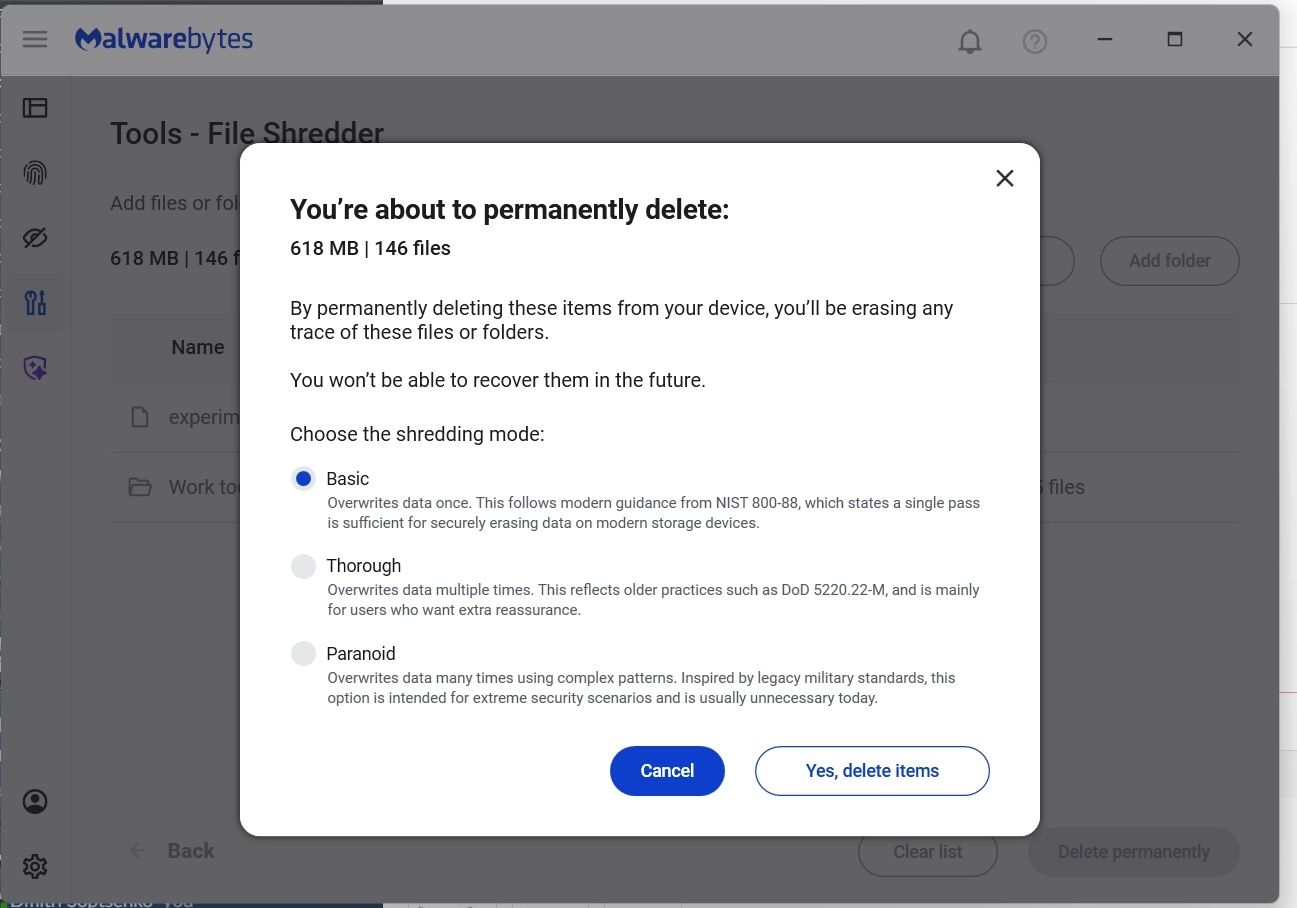
- You will be asked to confirm your request before File Shredder deletes the files
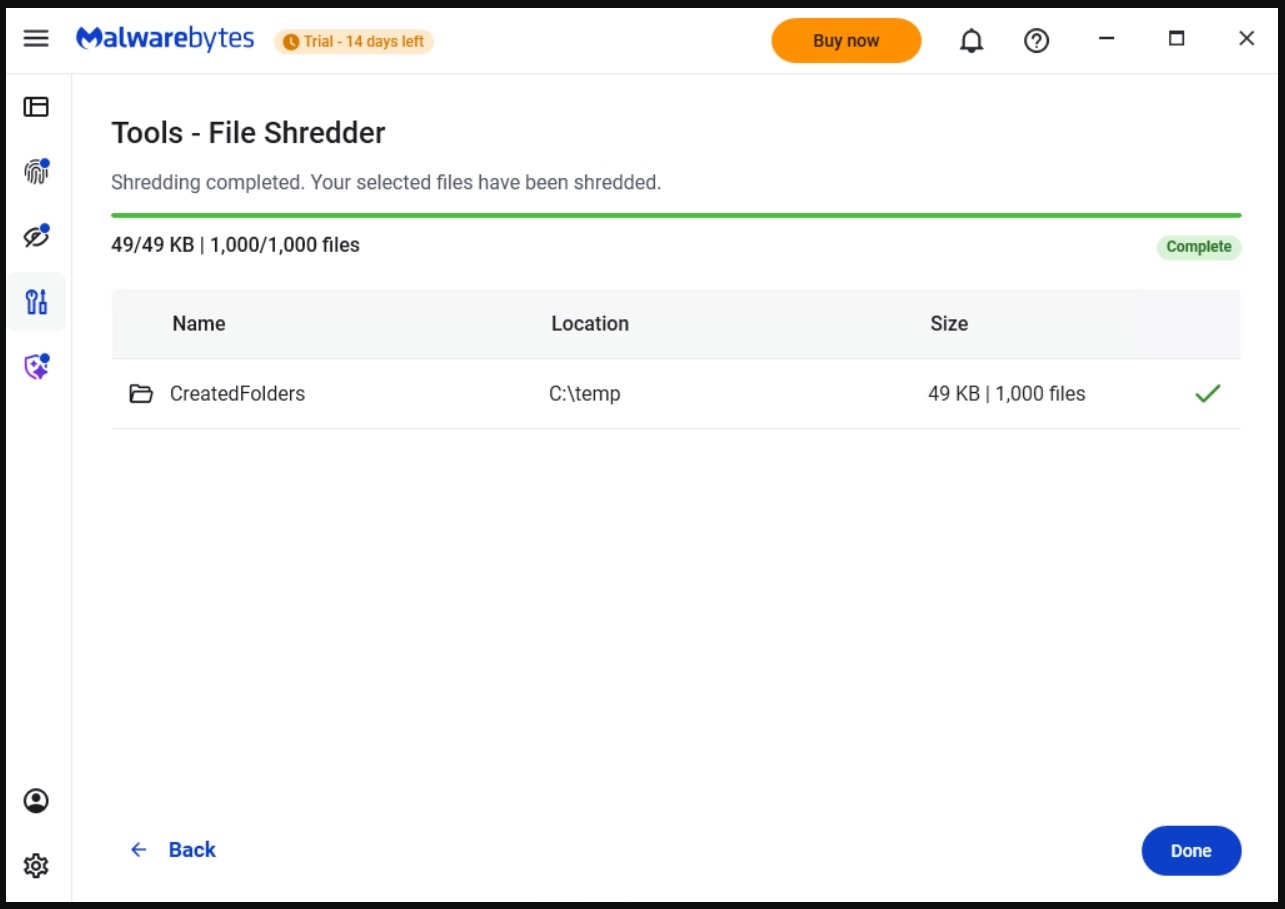
After your files are deleted by File Shredder you can move on, confident that the data can’t be accessed again.
Protection means your data is in your control
Cybersecurity isn’t just about blocking threats—it’s also about giving you control over your own data. File Shredder provides a way to do exactly that, helping you close the door on files that you no longer want on your devices.
Because when you’re done with a file, it should really be done.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
Supreme Court to decide whether geofence warrants are constitutional
Mar. 5th, 2026 10:54 amGoogle has weighed in on a court case that will decide the future of a powerful but contentious tool for law enforcement. The company submitted an opinion to the US Supreme Court arguing that geofence warrants are unconstitutional.
A geofence warrant is a form of “reverse warrant” that turns a regular warrant on its head. Police get a regular warrant when they want to target a particular person. With a reverse warrant, police don’t know exactly who they’re looking for. Instead, they ask someone (typically a technology company) for a broad data set about a group of unknown people based on some common behavior. Then they analyze that data set for potential suspects.
With a geofence warrant, that data set is defined by a location and a time window. Law enforcement officials obtain a list of phones that were in that area during that period. Every device that was inside the circle comes back in the results, even if nobody on that list has been suspected of anything. Proximity is the only criterion.
That’s how Okello Chatrie was charged with armed bank robbery in Virginia in 2019: His phone showed up in a geofence warrant covering 17.5 acres (larger than three football fields). He argued that this kind of search isn’t constitutional and shouldn’t have been used as evidence.
In 2024, the Fifth Circuit Court of Appeals agreed with him, overturning a Fourth Circuit ruling. Now prosecutors have taken the case to the Supreme Court, with parties due to make oral arguments on April 27.
The case has seen a flurry of amicus curiae briefs, which are opinions from interested expert parties that have no direct involvement in the case. One of these is from Google, which on Monday urged the justices to consider the geofence warrants unconstitutional because of their broad scope. It has objected to more than 3,000 of them on constitutional grounds in recent months.
Google’s brief stated:
“Many of these overbroad warrants swept in hundreds, sometimes even thousands, of innocent people. State and federal courts have repeatedly granted Google’s motions to quash these overbroad warrants.”
How the database gets built
Although Google is just one of many organizations that filed amicus briefs, its position is especially notable because it has historically collected so much location data. Its Timeline feature (formerly Location History) logs device position via GPS, Wi-Fi networks, Bluetooth, and mobile signals, including when Google apps aren’t being used, according to its policy page.
At the time of the Chatrie warrant, it was recording position as frequently as every two minutes. All of that fed a centralised internal database which held 592 million individual accounts. So responding to any geofence request required Google to search essentially the entire store before producing a single name, according to an analysis by privacy advocacy group EPIC, which also regularly submits amicus briefs on privacy cases.
Google moved Timeline storage from its own servers onto users’ devices in July 2025, closing the door to fresh cloud-based requests against its own systems. But the constitutional question survives for historical data and for any company that has not followed suit.
The warrant that grew and grew
A geofence warrant does not stay fenced, according to a separate brief that the Center for Democracy and Technology (CDT) filed in the case last week. It said Google’s standard response to warrants had three steps. First it would deliver an anonymized list of devices inside the geofence. Then, police could ask for movement data on chosen “devices of interest,” which could track them outside the geographic boundary and beyond the original time window. Finally, again without any further judicial approval, police could ask for subscriber-identifying information for whichever devices police chose to unmask.
In the Chatrie case, positioning data was imprecise enough that, as the district court found, the warrant may have included devices outside the intended area. According to the CDT brief:
“The Geofence Warrant could have captured the location of someone who was hundreds of feet outside the geofence.”
The CDT argues in its brief that this can expose the privacy of people going about their everyday lives, engaging in legal activities that they might not want others to know about. The warrant that scooped up Chatrie included a hotel and a restaurant.
Some of these requests are far broader. Google successfully challenged a warrant asking for the location history of anyone in large portions of San Francisco for two and a half days, it said. Google complained in its brief:
“No court would authorize a physical search of hundreds of people or places, yet geofence warrants sometimes do so by design.”
What can you do to stop yourself getting swept up in a geofencing search?
If your phone stores detailed location history with Google, that data may be included in geofence warrant responses. Limiting what gets saved can reduce how much location information exists in the first place.
There are two Google settings that matter: Timeline (Location History) and Web & App Activity. Turning off one does not automatically disable the other.
Timeline stores a detailed record of where your device has been, although it’s off by default. Web & App Activity can also log location signals when you use Google services like Search, Maps, or other apps.
Google provides instructions on how to review and disable these settings in its support documentation:
Google has previously settled lawsuits accusing it of misleading users about how location data is stored across these settings, so reviewing both controls is important.
Reverse warrants may not stop at location data
The implications of the case extend well past maps, though. The CDT brief warns that if courts endorse the logic behind geofence warrants, then law enforcement may try to apply the same approach to other large datasets held by technology companies, such as AI chatbot data. That’s a step the DHS has already taken, issuing what has been reported as the first known warrant for ChatGPT user data.
We don’t just report on privacy—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.
Cisco flags more SD-WAN flaws as actively exploited in attacks
Mar. 5th, 2026 05:32 amPhobos ransomware admin pleads guilty to wire fraud conspiracy
Mar. 5th, 2026 03:34 amNew Supe on Tap
Mar. 5th, 2026 12:09 amThe rumor mill is kicking into high gear.
Supposedly, Larritorious has made it known he's leaving in May.
Heiniken is following him out the door because he has no future without running cover for Larry.
Next up?
- Dana O'Malley
Yep, a DEI civilian with zero law enforcement experience aside from running the "Consent Decree" and an innate dislike of anything police related is the front runner for the top spot.
Conehead's biggest "fuck you" to the Department as he heads into (or bails out of) what promises to be a contentious re-election campaign.
About Those Punitive Damages
Mar. 5th, 2026 12:07 amAs most readers know, punitive damages CANNOT be paid by the City - it's the Law.
Hits like that come out of coppers' pockets. It has been common practice in the past that - after a verdict assessing such damages - Corp Counsel enters into negotiations pending an appeal whereby they'll try something like this:
- We're going to appeal this multi-million dollar verdict and tie it up in court for the next five years....but if you agree to drop the punitive damages against the Officers, we'll recommend to the City council that they approve this slightly smaller "settlement" and you'll get paid later this year. What you think?
And many times, the lawyers will tell their clients that a fast payout is the way to go.
This comment though....this would be bad news:
- From inside the 5th Floor, the Mayor is saying no deals. He feels it is time for the Police to feel the pain of paying their share of misconduct judgements. This will not be good for us.
We've known a few Officers who ended up on the wrong end of these judgements and it's not a good feeling knowing that a portion - no matter how big or small - of all your earnings are going to someone who had a better lawyer than Corp Counsel.
Read CWB
Mar. 5th, 2026 12:05 amTheir operation is literally the first place we go every day to see what's brewing. And it was a lot yesterday.
First up, another SAFE-T Act success story:
The man who shot and killed the father and son operators of a family jewelry store in Little Village late last year was AWOL from two felony cases at the time of the murders, prosecutors said Tuesday. And, they said, Muhammad Thomas was also wanted in one of those cases when he allegedly shot another victim during a carjacking attempt in 2023.
Thomas, 35, is now detained pending trial by order of Judge Rivanda Doss Beal on a host of felony charges, including two counts of first-degree murder.
Then an update on the Shots Fried at the Police earlier this week - and look! It's another parolee who should have been behind bars!
A man who got a sweetheart plea deal for a serious gun case in December is accused of trying to kill four Chicago police officers Monday morning in the Gresham neighborhood.
Sedrick Griffin, 31, is scheduled to appear at a detention hearing Monday afternoon at the Leighton Criminal Courthouse, where prosecutors will detail the allegations against him. Court records show he is on parole after serving less than a year in prison for being a felon in possession of a firearm.
And finally, another effort by politicians to hide how badly Illinois is being run by "reclassifying" criminal acts:
Some Illinois lawmakers want to rebrand fentanyl deaths as “poisoning” instead of “overdose,” but coroners say the change would force them to lie on death certificates.
Senate Bill 3014 would direct coroners and medical examiners to classify deaths involving fentanyl as “poisoning” instead of “overdose.” Under the bill, each fentanyl-related death would have to be reported separately to the Illinois Department of Public Health, and the department would be required to publish these fatalities distinctly in its monthly overdose reports, rather than grouping them with other drug overdoses.
The bill’s sponsor Sen. Sue Rezin (R-Morris), says the change is intended to reduce stigma and give families a more accurate way to describe the deaths of loved ones who unknowingly ingested fentanyl-laced substances.
“Too many angel families feel forced into silence because of the stigma surrounding… ‘overdose death,’” Rezin said. “This bill helps to elevate the conversation…and give families some peace in properly describing what happened to their loved ones, by renaming or reclassifying their death as a poisoning,”
By a poison that they willingly and voluntarily put into their own bodies, dumbass. Trust us, the family knew the deceased was a drug addict and they're probably relieved he's not around to burglarize the house and steal grandma's social security check.
This reminds us of that thing a few years ago:
- someone could be flying in an airplane....and the plane could hit an endangered condor....and the condor could break a window and someone was sucked out of the window....and as they fell 20,000 feet toward the ground, they bounced off a mountain causing a small avalanche....then they hit a tree and got impaled by some branches....then they hit the ground and a bunch of rocks from the avalanche crushed the remnants of their body into powder....and the police found the body parts, transported them to the coroner and notified the family, who said "He was coughing a little bit the week before he left"
Cause of Death - COVID.
Odd Endorsements
Mar. 5th, 2026 12:03 amThe FOP came out with endorsements for the upcoming primary (click for larger view):
Wasn't LaShawn Ford indicted for 17 felony counts of bank fraud a few years ago? And didn't he plead to one of the counts to avoid an embarrassing trial?And this Kwame fool - wasn't he instrumental in pushing the SAFE-T on Illinois, endangering citizens and cops alike?
Next thing you know, they'll be endorsing Conehead because he took great care of ILLEGAL ALIENS with money that could have funded the pension and services to actual citizens.
Can't Catch a Break
Mar. 5th, 2026 12:01 amWhat's the quote from the movie "Play it to the Bone"?
- If a man builds a thousand bridges and sucks one d#$%, they don't call him a bridge-builder... they call him a [Keesing Bandit]
Or something like that. This criminal has been fired for longer than he was the police....but he's still a "former officer:"
A former Chicago police officer was sentenced Tuesday to four years in prison for defrauding a low-income food program.
Prosecutors say Hassan “Eric” Abdellatif, 37, illegally billed $14 million to the federal Women, Infants and Children program, or WIC, as owner of the El Milagro Mini Market and Harding Grocery in Chicago.
Abdellatif, who lost his Chicago Police Department job after his 2021 arrest, asked for mercy before U.S. District Judge Jorge L. Alonso handed down his sentence at the Dirksen Federal Courthouse. Alonso also ordered Abdellatif pay $8 million in restitution.
Committed fraud from 2010 to 2018.
Hired two months after the last documented fraud in late 2018.
Fired in 2021, so off the job for almost five years now.
Still bringing discredit to the Department.
(no subject)
Mar. 4th, 2026 07:00 pmOnce they turn 30, they should be treated like they’re 60.
"A teacher at an elite high school in San Francisco has been placed on indefinite leave after allegations of sexist and fat-shaming questions included on ninth-grade Algebra I quizzes, according to administration officials and multiple media reports ...
'The amount of money you spend on a date varies inversely to how much they weigh. A typical girl that weighs 120lbs will cost you $55,' the math problem reportedly read. Students were then directed to first “derive the variation equation” and then asked how much they could expect to on a date “with Ashely who is $220lbs?” A third prompt asked students to calculate how much their date would need to weigh if they could only afford to spend $5."
Not all heroes wear thinking hats.
[This is a Guest Diary by Joseph Gruen, an ISC intern as part of the SANS.edu BACS program]
The internet is under constant, automated siege. Every publicly reachable IP address is probed continuously by bots and scanners hunting for anything that can be exploited or retrieved. It’s not because there is a specific target, but simply because that target exists. This type of behavior, known as opportunistic scanning, is one of the most prevalent and persistent threats facing internet-connected systems today. The opportunistic threat actor fires a series of large-scale automated probes at the entire internet and collects whatever responds. They are not after one person specifically; they are after anyone who left a door unlocked. This is the opposite of a targeted intrusion, where an adversary researches specific organizations, crafts custom tools, and maintains access while working quietly in the background.
This distinction matters enormously for defenders as a targeted attacker will adapt and persist when blocked, while an opportunistic scanner will simply move on to the next IP on its list. To understand how these automated actors operate, what they look for, how they find it, and what they do when they find it is to understand one of the most fundamental realities of modern internet exposure. On January 31, 2026, my DShield web honeypot recorded a short-lived surge in HTTP traffic behavior. This spike stood out from the normal day-to-day patterns reviewed for the month of January 2026. A single automated scanner generated nearly 1,000 requests in a 10-second window, systematically probing for sensitive files that are commonly left exposed by misconfigured or careless web server administrators. A mix of file enumeration and classic opportunistic vulnerability probes was recorded. The Kibana time picker was utilized, narrowed, and set to January 31, 2026, at 06:01:30 to January 31, 2026, 06:01:40.
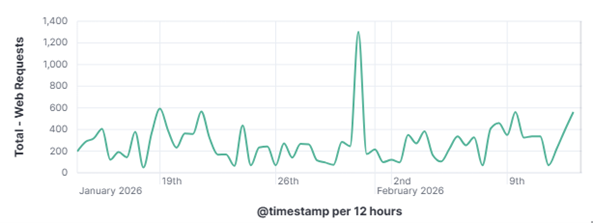
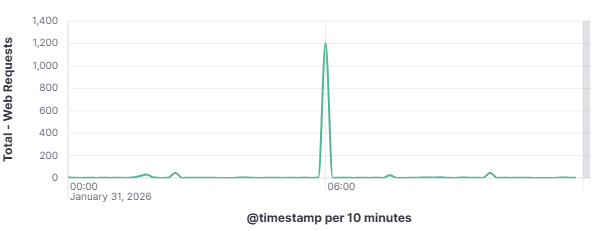
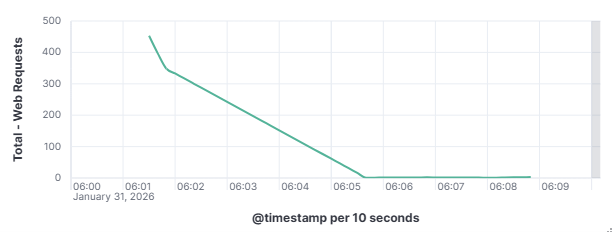
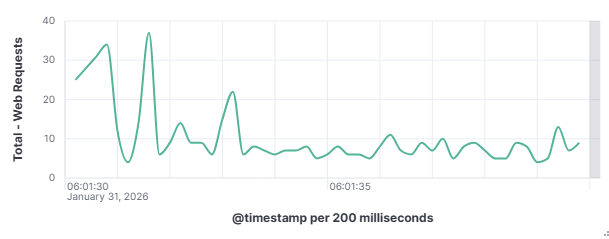
101.53.149.128 generated approximately 962 events (~52.91%) by itself which happened during that 10-second window. The top source (101.53.149.128) behaved like a broad-spectrum web scanner running a word list focused on accidentally exposed artifacts (compressed backups, database dumps, deploy bundles). Instead of flooding one URL repeatedly, it was testing hundreds of unique filenames once each.

Frequently requested file extensions included
.gz (255) - file is a compressed archive file created by the GNU zip (gzip) algorithm
.tgz (170) – file is a compressed archive file, commonly known as a "tarball," used primarily in Unix/Linux systems to bundle multiple files and directories into one file and compress them using gzip
A large set tied at 85 each: .bak, .bz2, .sql, zip, .7z, .rar, .war, .jar.
.bak - file is a common file extension used for backup copies of data, often created automatically by software
.bz2 - file is a single file compressed using the open-source bzip2 algorithm. Common in Unix/Linux, it offers high compression ratios, similar to .gz but usually slower with higher memory usage. These files are used for data compression and archiving.
.sql - file is a plain text file that contains code written in Structured Query Language (SQL). This code is used to manage and interact with relational databases, including creating or modifying database structures and manipulating data (inserting, deleting, extracting, or updating information).
.zip - file is an archive file format that combines multiple files into a single, compressed folder, reducing total file size for faster sharing and storage. It is widely used for organizing data and, in many cases, is supported natively by Windows and macOS without additional software.
.7z - file is a highly compressed archive format associated with the open-source 7-Zip software, designed for superior compression ratios using LZMA/LZMA2 methods, strong AES-256 encryption, and support for massive file sizes (up to 16,000 million terabytes). It is commonly used to group multiple files into a single, smaller package.
.rar - file (Roshal Archive) is a proprietary, high-compression archive format used to bundle, compress, and encrypt multiple files into one container.
.war - (Web ARchive) file is a packaged file format used in Java EE (now Jakarta EE) for distributing a complete web application. It is essentially a standard ZIP file with a .war extension and a specific, standardized directory structure.
.jar - JAR (Java ARchive) file is a platform-independent file format used to aggregate many Java class files, associated metadata (in a MANIFEST.MF file), and resources (like images or sounds) into a single, compressed file for efficient distribution and deployment. The format is based on the popular ZIP file format.
The above file extensions are all types of compression files, excluding the backup .bak, and .sql.
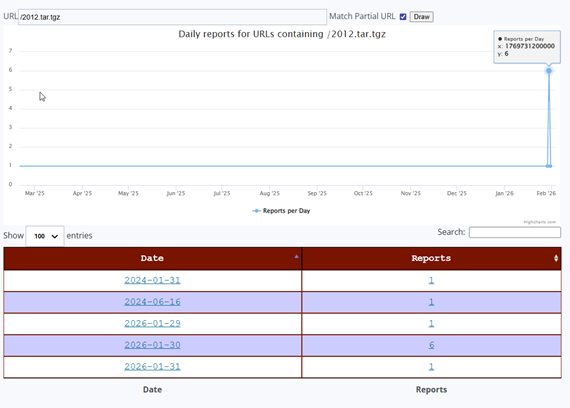
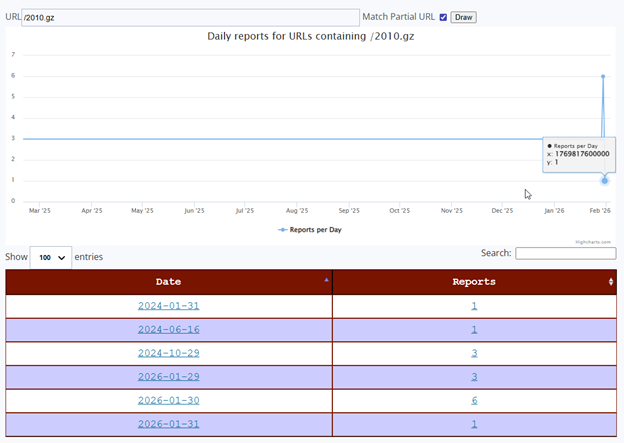
Both URLs share an almost identical reporting history. Each was first observed in the DShield sensor network on January 31, 2024, exactly 2 years before the 2026 campaign, with a single isolated report. A second isolated sighting for both occurred on June 16, 2024. After these sporadic early sightings, both URLs went completely dark across the entire sensor network from late 2024 through all of 2025, a stillness stretching over a year is a clear visible flat baseline on the ISC activity chart.
Then, beginning January 29, 2026, both URLs reappeared simultaneously across multiple sensors. The reporting pattern over those three days was identical for both URLs: 1 report on January 29, a peak of 6 reports on January 30, and 1 report on January 31, the date this sensor captured the activity. This synchronized, multi-day pattern across both URLs is the signature of a single coordinated scanning campaign sweeping across the internet.
The January 30 peak of 6 reports means that at least 6 independent DShield sensors worldwide were struck by this campaign the day before this sensor was hit. The January 31 capture represents the trailing edge of this wave, which has been building for three days across a network of honeypots. This corroboration is critical, as it confirms that what this sensor recorded was not a localized or random event, but part of a deliberately coordinated campaign that the multiple defenders around the world were observing simultaneously.
The fact that these URLs first appeared over two years earlier, in January 2024 and June 2024, indicates that this wordlist is not brand new. It has existed in some form for at least two years. However, the complete absence of reports throughout all of 2025 followed by a sudden concentrated burst in late January 2026 suggests the actor either went dormant and resumed, updated their infrastructure, or began deploying this wordlist at a significantly larger scale at the start of 2026. The January 2026 campaign represents the most sustained and globally distributed use of these URLs ever recorded in the ISC dataset.
The observed traffic spike captured by this DShield web honeypot on January 31, 2026, illustrates how quickly and efficiently automated opportunistic scanners can probe exposed web services for sensitive files. A single actor operating from 101.53.149.128 executed a rapid, wordlist-driven file enumeration campaign targeting year-based compressed archives and a broad set of sensitive file extensions, all via HTTP on port 80, with no SSH probing, no authentication attempts, and no multi-vector behavior of any kind. The honeypot telemetry provides valuable insight into these behaviors and reinforces the importance of secure configuration and continuous monitoring of Internet-facing services.
The retrospective DShield SIEM analysis confirmed the actor was narrowly focused. A dedicated web artifact harvester, not a general-purpose scanner. The ISC URL history data placed this local observation into global context, revealing a coordinated 3-day campaign that struck at least 6 independent honeypots worldwide on January 30, before reaching this sensor on January 31, the trailing edge of a wave the global DShield community was observing in real time.
The uniqueness of these URL patterns is the ISC dataset, combined with the structured sophistication of the wordlist and the precision of the actor’s web only behavior, suggests this represents either a newly scaled deployment of existing tooling or a freshly updated campaign targeting server backup artifacts. Early detection and reporting of such patterns contribute directly to the global threat intelligence ecosystem and allows defenders worldwide to strengthen their posture before campaigns mature.
Understanding what opportunistic attackers look for is critical for defenders. The presence of backup files, data exports, or deployment artifacts on production web servers can lead to immediate compromise without the need for sophisticated exploits. Even short exposure windows as little as the 10 second captured here are sufficient for automated scanners to identify and attempt to retrieve sensitive data.
[1] https://isc.sans.edu/weblogs/urlhistory.html?url=LzIwMTAuZ3oK
[2] https://isc.sans.edu/weblogs/urlhistory.html?url=LzIwMTIudGFyLnRnego=
[3] A. I. Mohaidat and A. Al-Helali, “Web vulnerability scanning tools: A comprehensive overview, selection guidance, and cybersecurity recommendations,” International Journal of Research Studies in Computer Science and Engineering (IJRSCSE), vol. 10, no. 1, pp. 8–15, 2024, doi: 10.20431/2349-4859.1001002.
[4] J. Mayer, M. Schramm, L. Bechtel, N. Lohmiller, S. Kaniewski, M. Menth, and T. Heer, “I Know Who You Scanned Last Summer: Mapping the Landscape of Internet-Wide Scanners,” in Proc. IFIP Networking 2024, Thessaloniki, Jun. 2024, pp. 222–230, doi: 10.23919/IFIPNetworking62109.2024.10619808.
[5] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Animal House
Mar. 4th, 2026 06:11 pm- I know its pedophiles and corporations but what's the third one?
- Jewdicial
"House kills effort to release all congressional sexual misconduct and harassment reports". В их возрасте они еще и за диффченками бегают, риспект и уважуха. Так выпьем за то чтобы наши желания мискондакта совпадали с нашими возможностями харрасмента.